Publications
- Liu, W., Wang, W., Chen, H., Wang, X., Lu, Y., Chen, K., Wang, X., Shen, Q., Chen, Y. and Tang, H., 2021, June. Practical and efficient in-enclave verification of privacy compliance. In 2021 51st Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN) (pp. 413-425). IEEE.
- Chen, H., Chen, H.H., Sun, M., Li, K., Chen, Z. and Wang, X., 2023. A Verified Confidential Computing as a Service Framework for Privacy Preservation. In 32nd USENIX Security Symposium (USENIX Security 23) (pp. 4733-4750).
- Reed, A.C. and Reiter, M.K., 2023, July. Optimally Hiding Object Sizes with Constrained Padding. In 2023 IEEE 36th Computer Security Foundations Symposium (CSF) (pp. 505-520). IEEE.
- Wang, Z., Guan, J., Wang, X., Wang, W., Xing, L., and Alharbi, F., 2023. The Danger of Minimum Exposures: Understanding Cross-App Information Leaks on iOS through Multi-Side-Channel Learning. In Proceedings of the 2023 ACM SIGSAC Conference on Computer and Communications Security (CCS 2023) (pp. 281-295).
- Zhao, S., Xu, P., Chen, G., Zhang, M., Zhang, Y. and Lin, Z., 2023. Reusable Enclaves for Confidential Serverless Computing. In 32nd USENIX Security Symposium (USENIX Security 23) (pp. 4015-4032).
- Zhou, L., Liu, Z., Zhang, F., and Reiter, M. CrudiTEE: A Stick-and-Carrot Approach to Building Trustworthy Signing Key Management with TEEs. In 6th Conference on Advances in Financial Technologies.
- Zhou, Q., Dang, S., and Zhang, D. Ctchecker: a Precise, Sound and Efficient Static Analysis for Constant-Time Programming. In Proc. of the European Conference on Object-Oriented Programming, 2024.
- Chen, H.H., Chen, H., Sun, M., Wang, C., and Wang, X., 2025. Picachv: Formally Verified Data Use Policy Enforcement for Secure Data Analytics. To Appear in 34th USENIX Security Symposium (USENIX Security 25).
Ongoing works:
- Chen, H., Zhou, Q., Yang, S., Han, X., Zhang, D., Zhang, F. and Wang, X., 2025. Agora: Open More and Trust Less in Binary Verification Service. In submission.
- Zhao, S., Wang, W., Li, N., Lin, Z., 2025. STYX: Collaborative and Private Data Processing Using TEE-Enforced Sticky Policy. In submission.
Open Source
Deflection
Deflection is an SGX shielding runtime (SGX middleware) that can run nearly unmodified C/C++ code securely. Other than Graphene-SGX, SCONE, Occlum, etc., it can protect the code secrecy and data confidentiality at the same time.
PoBF
Proof of Being Forgotten (PoBF) and PoBF-Compliant Framework (PoCF) prototypes.
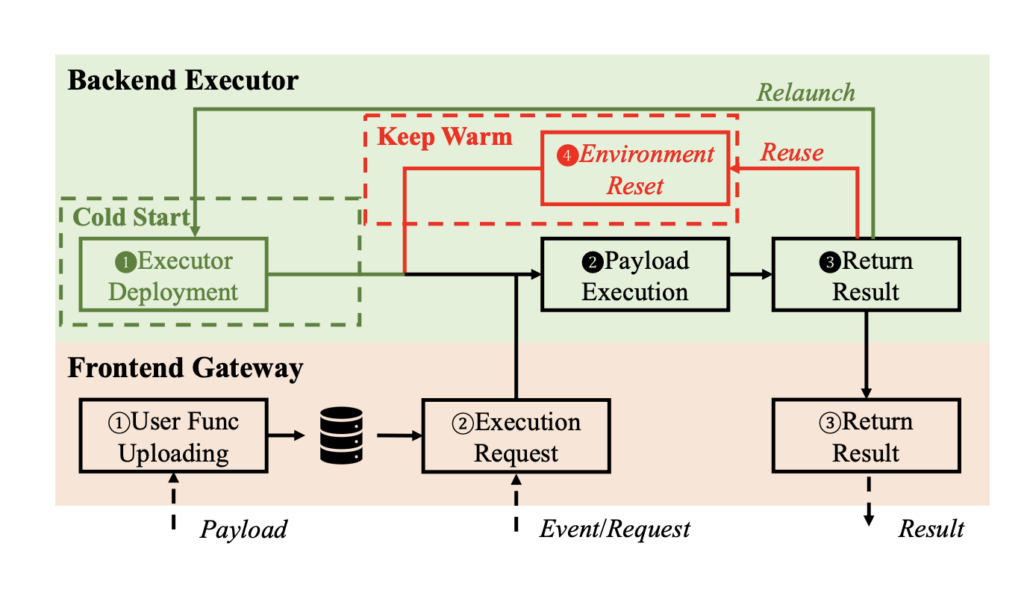
Reusable-Enclaves
This is a research project aims to solve the cold start problem without sacrificing the security by creating a method to securely reuse the enclave. The paper is accepted to 2023 USENIX Security Symposium.